Securing Businesses Across UK
Phishing Protection & Cyber Awareness Training
Prepare for Cyber Essentials
If you're unsure whether your business is ready for Cyber Essentials certification, our cybersecurity assessment services offer a thorough pre-assessment to help you identify and address any gaps. Our team will guide you through key requirements, ensuring you're fully prepared for a successful certification process.
Cyber Essentials Certification Process
We offer a simple and seamless process with a dedicated consultant to help you achieve Cyber Essentials Certification. Our cyber security consulting services ensure expert guidance throughout the certification journey.

PRE-ASSESSMENT
PRE-ASSESSMENT
Engage in detailed discussions with our specialists to assess your current cybersecurity measures and pinpoint areas for improvement.

ASSESSMENT
ASSESSMENT
Once the security controls are in place you will need to answer the self-assessment questions. We will then review and advise if any changes are required.

CERTIFICATION
CERTIFICATION
If your evaluation is successful, you will be notified and receive the Cyber Essentials certification.

RENEWAL
RENEWAL
The certification is valid for 12 months and will need to be renewed.
Cyber Essentials is available in two levels:
Level One
Cyber Essentials is an independently verified self-assessment
Cyber Essentials operates through a self-assessment questionnaire, where organizations respond to questions covering the assessment scope, employees, devices, and work locations. They also answer questions focused on the five core security controls: user access management, secure configuration, security update management, firewalls and routers, and malware protection. A board member or equivalent must approve the responses, which are then reviewed by an independent Assessor.
Implementing robust cyber security management services ensures that your organization meets these requirements effectively. For law firms, adhering to a comprehensive cyber security policy for law firms is crucial to safeguard sensitive client data and maintain compliance.
*Prices for Cyber Essentials are exclusive of VAT.

Cyber Essentials is priced according to the size of your organisation
Level Two
Cyber Essentials Plus is a technical audit of your IT systems
Cyber Essentials Plus is a technical audit of your IT systems. Completing the verified self-assessment questionnaire for Cyber Essentials is a prerequisite for achieving Cyber Essentials Plus. While both certifications share the same technical requirements, Cyber Essentials Plus includes a technical audit of your IT systems to confirm the controls are effectively implemented. This audit provides greater assurance of compliance with the scheme. The audit reviews a representative sample of user devices, all internet gateways, and any servers with internet-accessible services.
Engaging in comprehensive managed IT support services can aid in preparing for and successfully completing this certification process.

Cyber Essentials Plus is priced according to the size and complexity of your network

External & Internal Network Audit
Our Network Audit service provides a comprehensive overview of your organization’s security posture, helping you identify vulnerabilities and quantify risk levels across your network.
Internal Network Scan : Gain insights into your internal systems to detect hidden vulnerabilities and weaknesses within your infrastructure.
External Network Scan : Assess your perimeter defences to identify potential entry points that attackers might exploit.

UK GDPR is a vital aspect of your business
Small businesses also must adhere to the data protection principles, which include the same eight rights that apply to large businesses.
We can offer consultancy to venues to discuss how GDPR affects you and devise a plan to ensure that you are GDPR compliant in all areas of your organization. GDPR awareness training is the perfect first step for any organisation looking to achieve GDPR compliance.


Reliable Security Services

Automated Asset Management
Secure and efficient remote asset management through automation.

Penetration & Vulnerability Testing
Identifying security gaps through in-depth testing.

Solution-Oriented Reporting
Detailed Findings and Solution Proposals.
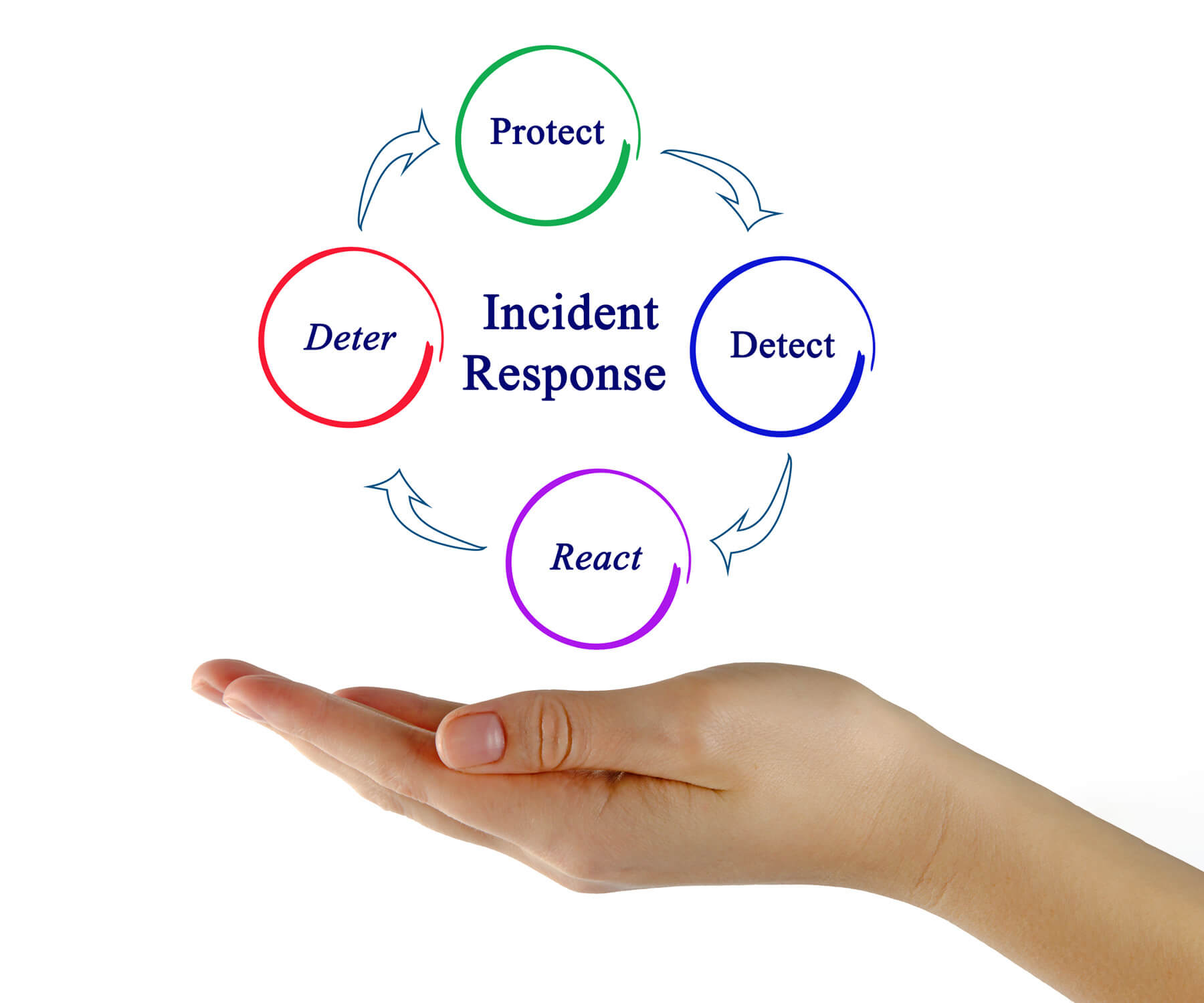
Intech Incident Response: Prepare, Prevent, and Protect
Intech Incident Response (IIR) ensures your organisation can effectively manage and recover from cyber threats.
Protect: Safeguard your data and systems.
Detect: Identify risks swiftly to minimise damage.
React: Act decisively to neutralise threats and restore operations.
Deter: Prevent vulnerabilities and discourage attackers.
Stay resilient against cyber challenges with IIR.
Cyber Security FAQ
For any questions regarding Cyber Essentials that are not covered below, please reach out to us at support@intechsecurity.co.uk.
- According to the UK government, achieving Cyber Essentials means your organization is protected from approximately 80% of cyber-attacks.
- Cyber Essentials certifications demonstrate that you are committed to cyber security and data protection to customers and stakeholders.
- Improves your organisation’s reputation and increases your chance of securing new business by showing you have robust cyber security measures in place.
Protects your Business against the majority of common cyberattacks and demonstrates to stakeholders your commitment to keeping their data secure and your business operational. This can increase business retention and attract new business. Increases the level of security of your systems and data, and puts processes in place to ensure this level continues – if not improves year on year. This helps to drive business efficiencies which in turn improves productivity through streamlined processes, reducing operational costs. Allows you to work on UK government contracts that involve the handling of personal and sensitive information. Reduces your insurance premiums by being able to prove your Business has increased its resilience to cyber threats.
This depends on the needs of your organisation, and also why you are putting it in place. For example, if you are looking to work with the public sector on government contracts then they will ask for Cyber Essentials as a minimum. If you want to demonstrate that your organisation is compliant with cybersecurity and takes data protection seriously, then you may also want to achieve Cyber Essentials Plus certification.
Further details on Cyber Essentials and the Cyber Essentials Plus scheme can be found at the National Cyber Security Centre website.
Yes, you can download a copy from the IASME website here, and further guidance is available from the National Cyber Security Centre here.
Once you’ve submitted and signed off your assessment a qualified assessor will then evaluate the responses against the criteria. If you meet the FIVE core requirements, you will pass and receive certification.
Yes, you’ll get feedback, we will supply a report with the answers you gave along with the assessor feedback. This will help you improve your security so you can achieve certification in the future.













